Cyberthreats keep CEOs awake at night
These companies that you deal with every day, chances are they had been victimized by hackers several times before.
Indeed, long before the Russia-Ukraine crisis, a war in cyberspace had already been keeping CEOs awake at night. It’s an arms race between the “good” guys and the “bad” guys, whose attacks damage businesses and hurt consumers as well as the global economy.
Based on IBM’s 2022 “Cost of a Data Breach Report,” which surveyed 550 organizations across 17 countries and 17 industries, 83 percent have had more than one data breach and just 17 percent said it was their first time to deal with hacking.
For consumers, it’s like being robbed: 60 percent of data breaches have led to increases in prices of goods and services sold by the victimized firms.
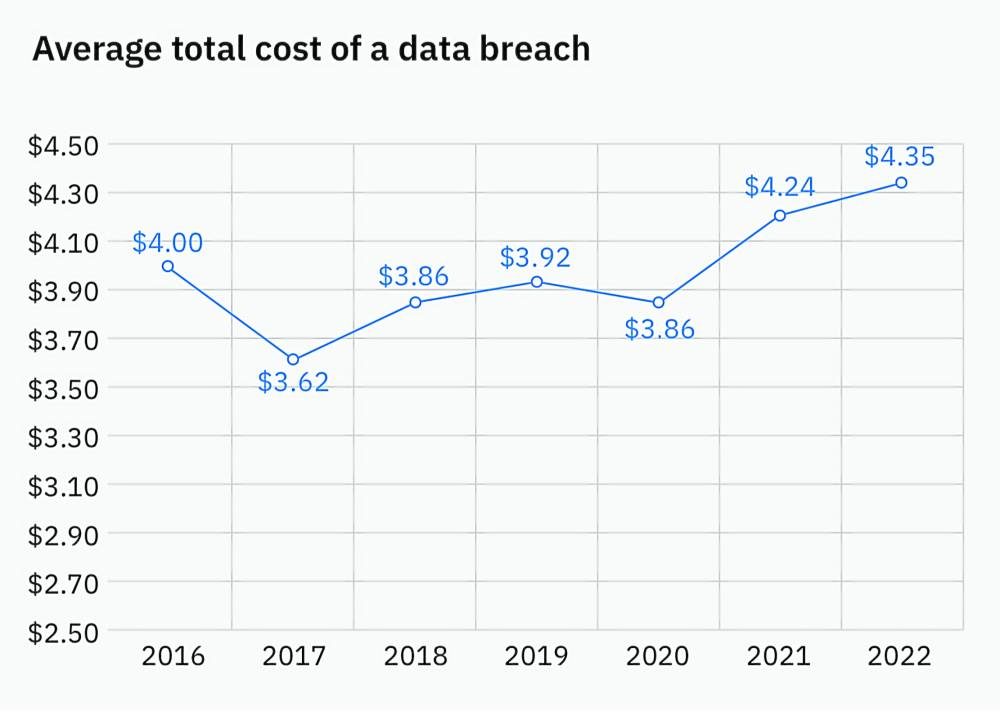
The report, which was based on data culled by Ponemon Institute, estimates average cost of a data breach at $4.35 million, the highest in the last 17 years since the survey began.
In Southeast Asia alone, the average cost of hacking is $2.87 million, likewise an all-time high.
When remote working is a factor causing the data breach—like when credentials are stolen because that carefree employee brought that laptop to work from the beach—the breach tends to be $1 million costlier.
Just in the last two years, as the world grappled with lockdowns, the cost of data breach rose 12.7 percent.
“The volume and velocity of attacks and bad activity are so high that humans can’t keep up with it,” Paul Burton, IBM Asia-Pacific general manager, says in an interview with Inquirer at the tech giant’s Philippine office in BGC. “What has to happen is you have to have AI (artificial intelligence) and technology to keep up with it in real time.”
About 10 percent of the $100-trillion global economy, or a whopping $10 trillion, is the estimated amount of money siphoned off by organized cybercriminals each year, according to research firm Cybersecurity Ventures. That means if cyberterrorists were a country, it would be the third largest next to the United States and China.
277 days to discover, address hacking
The IBM study estimates that it now takes about 277 days to identify and contain a data breach versus 287 days in 2021. A baby would have grown full term in the mother’s womb by the time a typical company discovers and addresses a cyber attack.
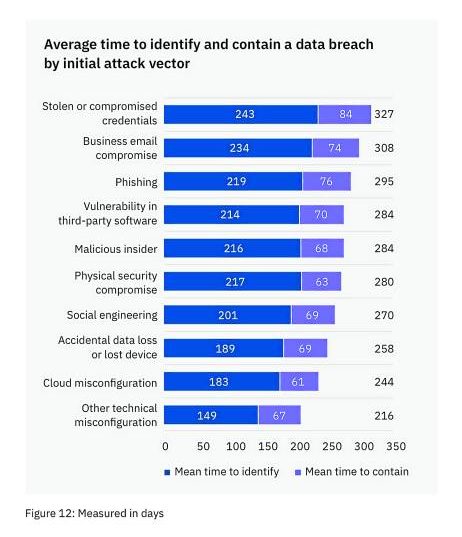
Specifically, it takes an average of 207 days to identify the breach and another 70 days to contain it. The length of time varies by attack vector.
The study identifies stolen or compromised credentials as the most common initial attack vector; this is blamed for 19 percent of breaches. Phishing follows with a share of 16 percent; cloud misconfiguration, 15 percent and vulnerability at third-party software, 13 percent.
Stolen or compromised credentials take the longest time to identify and contain (327 days), followed by breaches caused by business email compromise (308), phishing (295) and vulnerability at third-party software (284).
Asia is the most attacked region in the world “because there’s so much going on here,” Burton says.
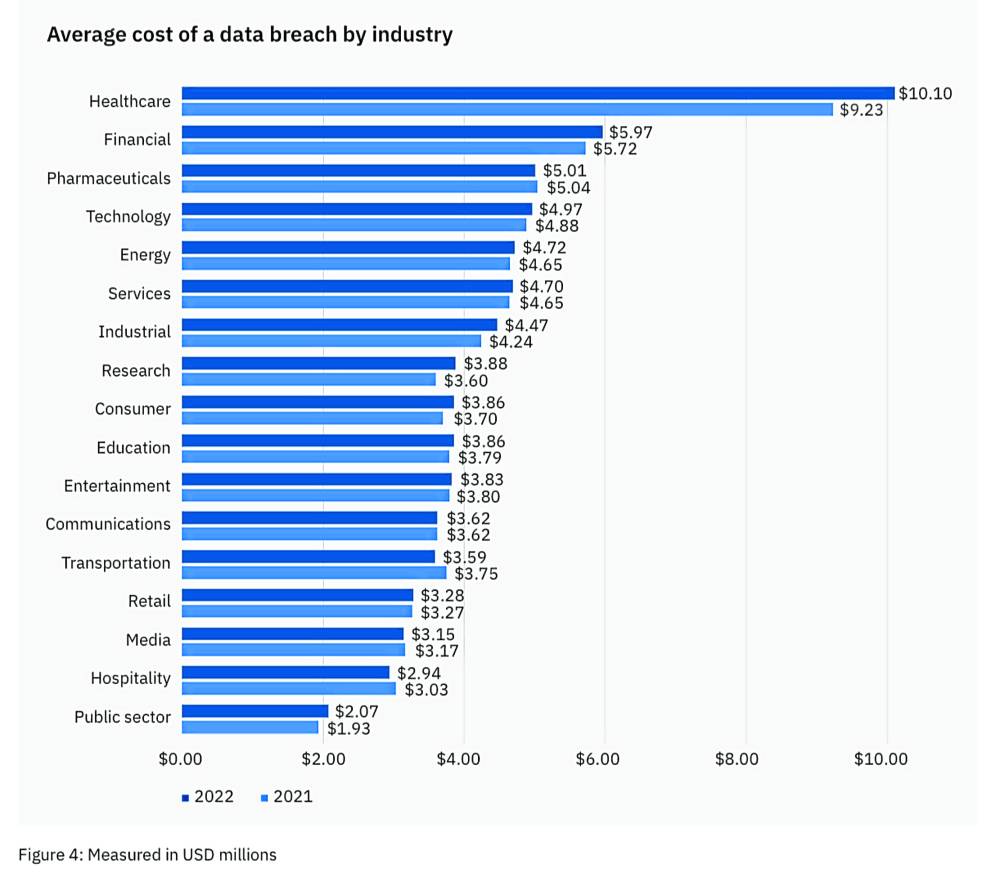
For the 12th year in a row, the IBM report showed health care has the highest cost of breach based on industry category, averaging $10.1 million. This is followed by financial services ($5.97 million), pharmaceuticals ($5.01 million), technology ($4.97 million) and energy ($4.72 million).
Companies that are just starting their digital transformation and migrating to the cloud are particularly vulnerable, especially if they do so without securing their systems first. Based on the IBM study, 45 percent of breaches occurred in the cloud.
Burton shares IBM’s strategy to counter cyberthreat in Asia-Pacific.
- Look at architectural practices and design it with security in mind.
- Assume a a philosophy of “zero trust.”
- Deploy AI, tools and smart people.
With these three imperatives, Burton says even if a bad guy gets in, he can be locked out before wreaking havoc on the system. Instead of nine months, a crisis can be detected and averted in 15 minutes or less.
AI is particularly important in recognizing the attack in real time, he says. Then, analysts and IT experts interpret the results.
The philosophy of zero trust is at the core of this strategy.
“We assume that you’re not allowed to see or do anything. And so every resource, every access point, everything is locked down. Only if you have a specific credential to gain access to that resource do you get in and if you get access to that resource, it doesn’t mean you get access to anything else. You have to have more credentials as you go along,” he explains.
“I’ve talked with several senior global 50 CEOs and I asked them what’s on their mind and what keeps them awake at night. It’s cyber(security). It’s bad,” he adds. “The repercussions are really severe and so everyone is investing in keeping the bad guys out.”
The good news is that the good guys are working together to safeguard cyberspace. They have a system for flagging and sharing malicious internet protocol addresses.
For its part, IBM is investing about $2 billion to remain at the top of its game and help companies fortify themselves against constant cyberthreats.
“The field is changing so quickly, you’ve got to keep up with it. If you’re not investing significant money, you’re going to fall behind,” Burton says.